Ly Lo Cong, a Senior consultant at Clever Age and our partners (SAP and Reachfive) join us in our interview about a key technology for delivering a personalized customer experience : CIAM.
“Hello, my name is Ly Lo Cong, I am a Senior consultant at Clever Age Canada.”
What is the purpose of deploying a CIAM ?
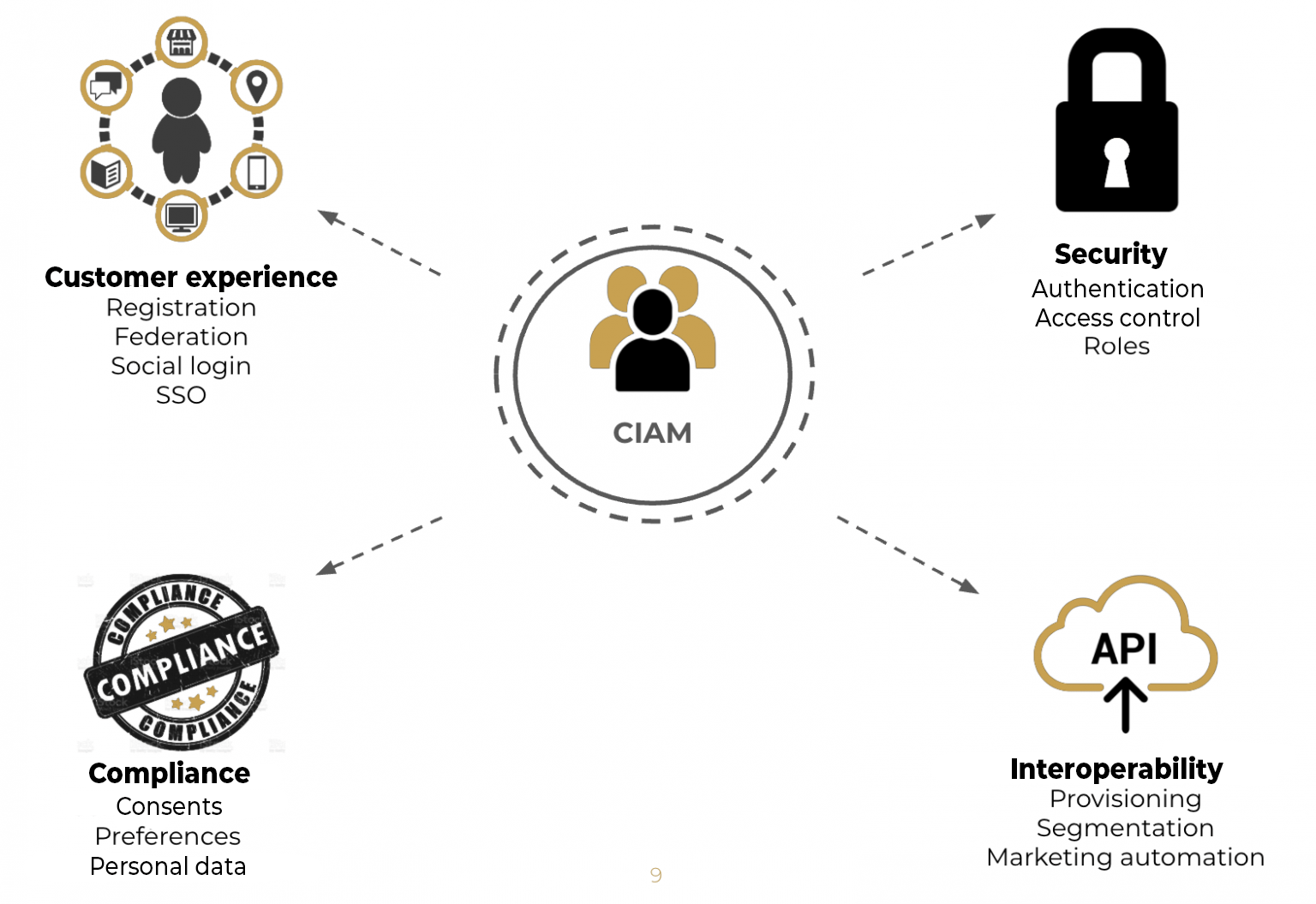
“A CIAM allows users’ digital identities to be centralized within a repository and to unify authentication and the user experience on different channels and devices.”
What are the objectives and challenges of our clients with the implementation of this service ?
“The goal for a company is to improve the customer experience through a unified omni-channel authentication to have a better control of its users’ private data by managing compliance with data protection regulations. Moreover, to benefit from a strong and scalable solution that allows them to optimize data exchanges between the applications in charge, to collect, enrich or even normalize it.”
Can you tell us more about the place of CIAM in the global architecture of a digital IS ?
“The CIAM is the service layer that sits between the various contact channels and the other service layers and repositories of a global architecture. It will allow to connect the user, to collect his data, then to distribute them to the different IS applications in charge of processing him such as a CRM, a DMP or even marketing automation.”
What about the overall functional scope of a CIAM project ?
“The CIAM will cover the main functionalities related to the user’s digital identity. All the authentication and registration part that can be found on the sites, with also the possibility to have a unique authentication between the different applications thanks to SSO, social logging via Facebook,Google or other social networks. CIAM also offers multi-factor authentication to improve security and it also offers fine-grained management of personal data and consent.”
What could be included in the customer information repository ?
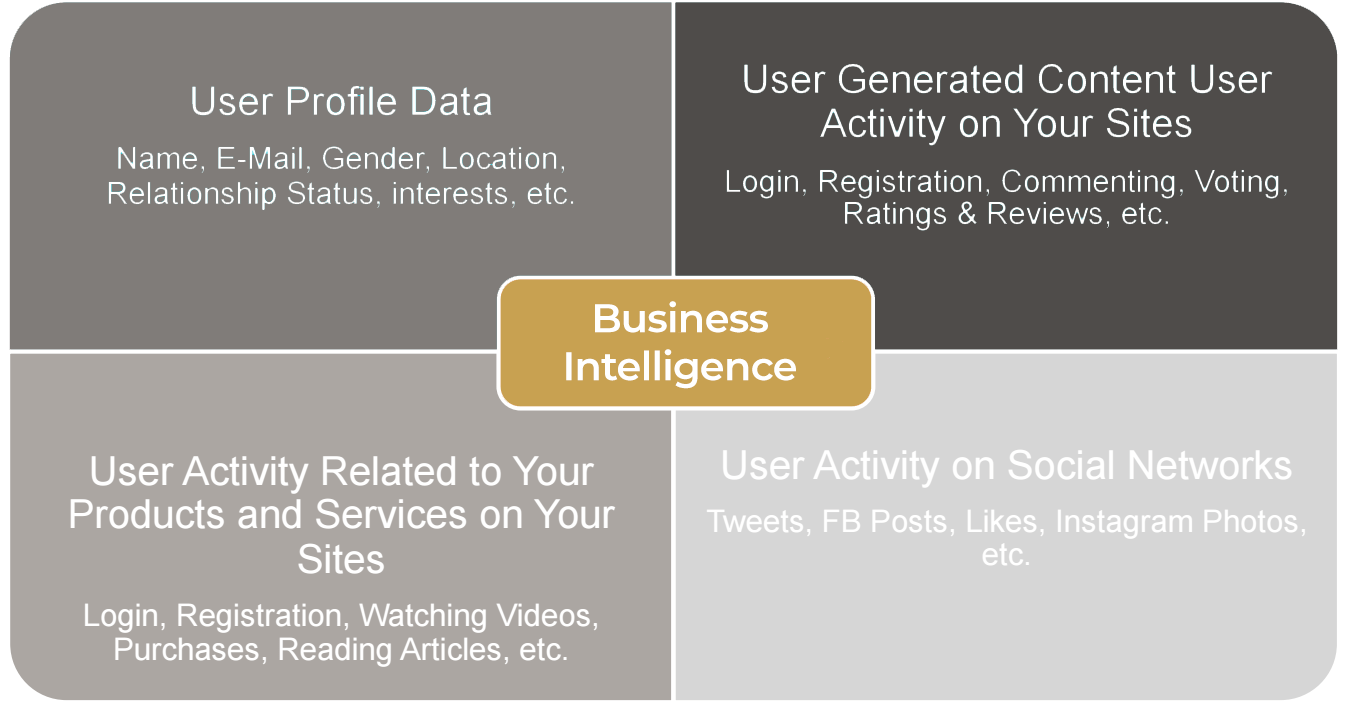
“We can find different types of data. We can have explicit data coming directly from the user, such as email address, name, password, etc. Implicit data such as navigation information can be stored, here, user type and it also stores data from social networks.”
How a CIAM project works, how to start a CIAM project ?
“You know if you should embark on a CIAM project when you start to have user data all over the place on the different applications.Different passwords for the same user. Duplication of personal data CIAM will above all make it possible to unify data and make the digital experience the digital experience smoother for users.”
Would you systematically go through a project scoping phase ?
“Yes,there are several elements that need to be determined during a scoping phase before the implementation phase can begin. For example, the data model that will be stored in the CIAM, to work on the data migration strategy, especially for passwords which, depending on their complexity may be impossible to migrate. It is also necessary to define the data flows between the CIAM and the other systems that will process this data. There is also the whole strategy of supporting the change of the user. If this offer should change your password, change the way you log on to the website.”
What are the key steps in the design phase of a CIAM project ?
“First of all, this is done through workshops where we will receive and validate the user paths related to identity management.Registration, authentication, account management. Then, we do technical workshops to define the target architecture that will take into account the integration of CIAM and to identify the applications that will have to interface with the tool. And another important step of the design phase, as I said, on the data migration strategy.”
What are, in your opinion, the essential deliverables of a CIAM design phase ?
“At the end of the design phase, we must have at least a functional backlog, technical specifications and UX/UI mockups for the integration of the CIAM screens.”
In the implementation phase, what do you consider to be the major steps of the implementation ?
“The first step is to the configuration of the CIAM tool to take into account the specificities of the project. SSO configuration, password policy, transactional email settings.Then, there is the front-end development with the implementation of forms, the display of error messages on the front-end error messages on the front, etc.And back development for the implementation of data exchanges via the CIAM API.”
